SAP System Disaster Recovery Service
With the promotion and popularization of ERP strategies in various industries, enterprises are becoming more and more dependent on information systems. As the core of information systems, databases play an important role, especially in some industries that have high requirements for data reliability, such as banking, securities, telecommunications, etc. If unexpected shutdown or data loss occurs, the losses will be very heavy or even devastating. sexual.
To this end, database administrators should develop detailed database backup and disaster recovery strategies based on specific business requirements, and rigorously test every possible scenario by simulating failures. Only in this way can high availability of data be guaranteed. Database backup is a long-term process, and recovery is only performed after an accident. Recovery can be regarded as the reverse process of backup. The degree of recovery depends largely on the backup situation. In addition, the correct steps taken by the database administrator during recovery also directly affect the final recovery results.
Decision specifically targets the particularities of the SAP system to provide customers with a complete, safe, and fast backup and disaster rescue solution, and promises 7x24-hour disaster rescue services to minimize customer risks.
• Database system (Oracle/DB2/SQL Server/Sybase/HANA) disaster recovery
• SAP system disaster recovery
1. Overall architecture requirements of disaster recovery system
2. Comparative analysis of disaster recovery technologies
Traditional disaster recovery solutions usually use scheduled backups, which cannot completely solve the problem of business continuity. However, more and more users want to ensure that their IT systems continue to run 24/7, which has triggered people's interest in CDP products. Strong attention. The concept of CDP was first born in 2005. Later, the debate about true and false CDPs raged, and CDP products were divided into two categories: One product still uses a scheduled backup model, but the backup time window has become smaller, from incremental backup once a day to one hour. Do it once or even once every half an hour. People call this CDP product Near CDP (Near CDP); another product called True CDP (Ture CDP) can completely eliminate the backup window (under an ideal hardware environment). ), RPO is zero, which is business continuity in the true sense.
CDP once caused a craze in the Chinese market. After that, many hardware manufacturers claimed to have introduced CDP functions into their storage systems. CDP seemed to have become the most common function and lacked topicality, so the popularity gradually waned. In 2011, the CDP technical group of SNIA (Global Storage Network Industry Association) published a technical document of CDP, which clearly pointed out the three elements of CDP: it can capture any data changes, and it can at least be backed up to another place (off-site storage). disaster) and can be restored to any point in time. Only CDP products that meet all three requirements above can be called true CDPs. According to such standards, replication technologies (synchronous and asynchronous mirroring, etc.), snapshot technologies (pointer snapshots, split mirror snapshots, etc.) and any planned backup with a backup window are not CDP products. "It can be seen that CDP can definitely achieve real-time backup with zero RPO, but the product that can achieve real-time backup may not be CDP, because the so-called real-time backup product may not be able to achieve recovery to any point in time.
3. Technical principles and characteristics
Real-time incremental backup principle: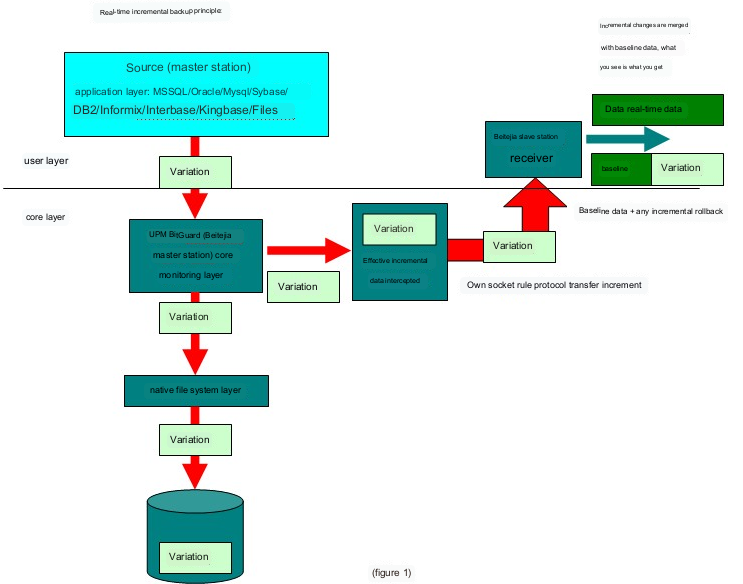
the
As shown in Figure 1, when the application changes data to the database, a filtering file system is added between the application layer and the local file layer. This system will monitor and backup the source (the backup source can be a database or a File or hard disk) related data has changed? If so, the system will copy the data change record in sequence and transfer it to the backup machine using the socket rule protocol between the backup master and slave stations. After the data changes are transmitted to the backup machine, one copy is recovered in real time with the previous data to form a copy of the latest immediately available data, and the other copy is stored in the .mydata file in its own format for data rollback.
Arbitrary rollback principle: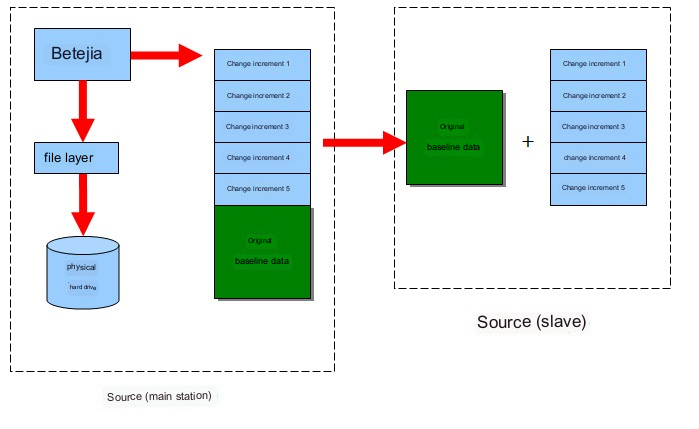
As shown in Figure 2, when the software runs for the first time, it will take the existing data as the "baseline data" for a full backup. After the full amount is completed, it will first store the same "baseline data" in the backup directory of the slave station.
Its backup special will copy the data changes it cares about to the backup directory of the slave station in order, but it will not be merged with the baseline data, and will only be stored in the log file in its own format. When a rollback operation is required, a rollback list is obtained by reading the timestamp of the changed data in the log, which contains all incremental changes after the full amount. Select any one of the points to perform the recovery operation, and the final execution will be the actual data changes on the standby disk.
Technical features:
Whether it is database backup, file backup or operating system backup, the latest CDP standard technology is adopted: all file access operations are captured in real time by implanting file filtering drivers in the core layer of the operating system. For files that require CDP continuous backup protection, when the CDP management module intercepts its rewriting operation through the file filter driver, it will automatically back up the changed part of the file data together with the current system time stamp (System Time Stamp) to the backup machine in advance. Therefore, any file data change will be automatically recorded, so it is called continuous data protection (CDP).
1) Based on database-level and file-level backup.
2) The target database is available during backup. After the target database goes down, the backup database on the backup machine can take over.
3) There is a database rollback mechanism at any point to ensure that when the main file is damaged, the backup database and files are still available.
4) Fast speed and strong real-time performance.
5) The backup is safe and reliable. If the main database file is damaged by a virus or the disk is damaged, the backup database can be arbitrarily rolled back to the data before the damage.
6) The main database can back up data to multiple targets at the same time, and the same backup machine can also back up data from multiple main databases at the same time. That is, it supports one-to-many and many-to-one.
7) It has nothing to do with the structure of the tables in the database and has no restrictions.
8) Do not make any modifications to the applications in the database.
9) Low requirements for backup lines.
10) There is no pressure on the main server. The system adopts a message mechanism, which is only triggered when the database changes, and only the changed part of the database is transmitted, which is different from file examination and polling of data tables.
11) Complete database backup: such as TABLES (table), DIAGRAMS (relationship diagram), VIEWS (view), STOREDPROCE (stored procedure), USERS (user), ROLES (role), RULES (rule), DEFAULTS (default) , USER DEFINED (user-defined), etc.
12) Universally applicable to all operating systems and database environments, supporting Linux, Windows, Unix operating systems and various mainstream databases.
the
4. Scheme design
Solution deployment instructions:
The database and file master modules of the UPM disaster recovery backup system are deployed on the two local application servers of "Production Center A".
Run the UPM disaster recovery backup system database and file slave module on other local computer room backup servers to achieve real-time data backup.
Under normal circumstances, all the data in the two application system servers in "Production Center A" are backed up in real time to the backup server storage in "Backup Center B" to ensure zero data loss, because this technology uses infinite incremental transmission, Therefore, even if it is transmitted remotely, it will not occupy too much bandwidth.
When the database data and file data of any application system server are wrong or lost due to logical errors (operating errors, mistaken deletion, etc.), the corresponding rollback data in "Backup Center B" can be restored at any time. The data at the rollback point is rolled back, and the data at the rollback point is guaranteed to be complete and available, and the data can be restored to the most recent complete state when the data is incomplete.
When any application system server suffers from hardware damage and data loss, after the server is repaired or replaced with a new server, it can be quickly restored to the previous complete state through the backup disaster recovery system, including applications, database data, raid, etc.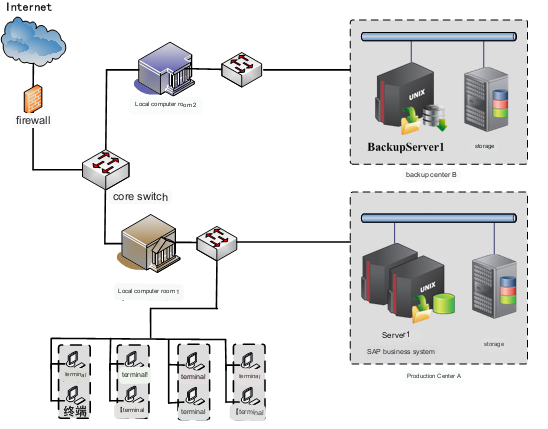
(image 3)
The proposal of this scheme fully considers the informatization characteristics of Sunrise Eastern Solar Co., Ltd. Based on the latest, most advanced and most stable technology, it adopts the most economical deployment mode and realizes a high disaster recovery backup Level of protection. It ensures zero data loss. When a logical error or hardware damage occurs, 100% data recovery can be achieved by rolling back at any point in time.
Real-time synchronization protection of important data on each server
Automatically monitor the database, continuously capture and backup data changes, as long as the data in the database changes, it will be backed up in real time and accurately. The security of data is ensured. Once data is lost or damaged, the data can be quickly restored from the backup machine.
The master database and the slave database can be synchronized in real time, eliminating the problem of interval backup loss in backup software. UPM also provides a complete no-data-loss mode and a business data correction method within seconds of loss.
Implementation of application switching within one minute when disaster occurs
When the main server goes down unexpectedly, the backup machine can take over the IP of the main server within one minute, provide all external services, ensure the continuity of the core business, and provide 365 days, 7*24 hours of uninterrupted business protection.
Implementation of original system recovery after disaster
After a disaster occurs, the original system must be restored as soon as possible. The reverse process of data disaster recovery and replication is performed during recovery, that is, reverse synchronization from the disaster recovery center to the primary data center. After the synchronization is completed, the application can be switched, and the entire system is restored to its original state.
Implementation of data recovery at any time for data logic errors
Data can be quickly restored according to any number of operation steps or time points, and return to any state of the database, so that data before accidental deletion or damage can be retrieved. During the recovery process, not only the integrity of the data is ensured, but the integrity of the event is also ensured. Solved the data logic error.
To this end, database administrators should develop detailed database backup and disaster recovery strategies based on specific business requirements, and rigorously test every possible scenario by simulating failures. Only in this way can high availability of data be guaranteed. Database backup is a long-term process, and recovery is only performed after an accident. Recovery can be regarded as the reverse process of backup. The degree of recovery depends largely on the backup situation. In addition, the correct steps taken by the database administrator during recovery also directly affect the final recovery results.
Decision specifically targets the particularities of the SAP system to provide customers with a complete, safe, and fast backup and disaster rescue solution, and promises 7x24-hour disaster rescue services to minimize customer risks.
• Database system (Oracle/DB2/SQL Server/Sybase/HANA) disaster recovery
• SAP system disaster recovery
1. Overall architecture requirements of disaster recovery system
- Build an open, industry-standard data disaster recovery and backup center that can support future system development.
- The system has advanced design, reasonable structure, economical and practical, stable operation, convenient operation, and the plan is forward-looking.
- Ensure that the main system can start the business takeover system within one minute in the event of a disaster to ensure uninterrupted normal operation of the business.
- Ensure that the data backup system is safe and reliable. When a data error occurs, the data can be restored to any desired point in time.
- Able to realize remote disaster recovery and backup functions.
2. Comparative analysis of disaster recovery technologies
Traditional disaster recovery solutions usually use scheduled backups, which cannot completely solve the problem of business continuity. However, more and more users want to ensure that their IT systems continue to run 24/7, which has triggered people's interest in CDP products. Strong attention. The concept of CDP was first born in 2005. Later, the debate about true and false CDPs raged, and CDP products were divided into two categories: One product still uses a scheduled backup model, but the backup time window has become smaller, from incremental backup once a day to one hour. Do it once or even once every half an hour. People call this CDP product Near CDP (Near CDP); another product called True CDP (Ture CDP) can completely eliminate the backup window (under an ideal hardware environment). ), RPO is zero, which is business continuity in the true sense.
CDP once caused a craze in the Chinese market. After that, many hardware manufacturers claimed to have introduced CDP functions into their storage systems. CDP seemed to have become the most common function and lacked topicality, so the popularity gradually waned. In 2011, the CDP technical group of SNIA (Global Storage Network Industry Association) published a technical document of CDP, which clearly pointed out the three elements of CDP: it can capture any data changes, and it can at least be backed up to another place (off-site storage). disaster) and can be restored to any point in time. Only CDP products that meet all three requirements above can be called true CDPs. According to such standards, replication technologies (synchronous and asynchronous mirroring, etc.), snapshot technologies (pointer snapshots, split mirror snapshots, etc.) and any planned backup with a backup window are not CDP products. "It can be seen that CDP can definitely achieve real-time backup with zero RPO, but the product that can achieve real-time backup may not be CDP, because the so-called real-time backup product may not be able to achieve recovery to any point in time.
3. Technical principles and characteristics
Real-time incremental backup principle:

the
As shown in Figure 1, when the application changes data to the database, a filtering file system is added between the application layer and the local file layer. This system will monitor and backup the source (the backup source can be a database or a File or hard disk) related data has changed? If so, the system will copy the data change record in sequence and transfer it to the backup machine using the socket rule protocol between the backup master and slave stations. After the data changes are transmitted to the backup machine, one copy is recovered in real time with the previous data to form a copy of the latest immediately available data, and the other copy is stored in the .mydata file in its own format for data rollback.
Arbitrary rollback principle:

(figure 2)
As shown in Figure 2, when the software runs for the first time, it will take the existing data as the "baseline data" for a full backup. After the full amount is completed, it will first store the same "baseline data" in the backup directory of the slave station.
Its backup special will copy the data changes it cares about to the backup directory of the slave station in order, but it will not be merged with the baseline data, and will only be stored in the log file in its own format. When a rollback operation is required, a rollback list is obtained by reading the timestamp of the changed data in the log, which contains all incremental changes after the full amount. Select any one of the points to perform the recovery operation, and the final execution will be the actual data changes on the standby disk.
Technical features:
Whether it is database backup, file backup or operating system backup, the latest CDP standard technology is adopted: all file access operations are captured in real time by implanting file filtering drivers in the core layer of the operating system. For files that require CDP continuous backup protection, when the CDP management module intercepts its rewriting operation through the file filter driver, it will automatically back up the changed part of the file data together with the current system time stamp (System Time Stamp) to the backup machine in advance. Therefore, any file data change will be automatically recorded, so it is called continuous data protection (CDP).
1) Based on database-level and file-level backup.
2) The target database is available during backup. After the target database goes down, the backup database on the backup machine can take over.
3) There is a database rollback mechanism at any point to ensure that when the main file is damaged, the backup database and files are still available.
4) Fast speed and strong real-time performance.
5) The backup is safe and reliable. If the main database file is damaged by a virus or the disk is damaged, the backup database can be arbitrarily rolled back to the data before the damage.
6) The main database can back up data to multiple targets at the same time, and the same backup machine can also back up data from multiple main databases at the same time. That is, it supports one-to-many and many-to-one.
7) It has nothing to do with the structure of the tables in the database and has no restrictions.
8) Do not make any modifications to the applications in the database.
9) Low requirements for backup lines.
10) There is no pressure on the main server. The system adopts a message mechanism, which is only triggered when the database changes, and only the changed part of the database is transmitted, which is different from file examination and polling of data tables.
11) Complete database backup: such as TABLES (table), DIAGRAMS (relationship diagram), VIEWS (view), STOREDPROCE (stored procedure), USERS (user), ROLES (role), RULES (rule), DEFAULTS (default) , USER DEFINED (user-defined), etc.
12) Universally applicable to all operating systems and database environments, supporting Linux, Windows, Unix operating systems and various mainstream databases.
the
4. Scheme design
Solution deployment instructions:
The database and file master modules of the UPM disaster recovery backup system are deployed on the two local application servers of "Production Center A".
Run the UPM disaster recovery backup system database and file slave module on other local computer room backup servers to achieve real-time data backup.
Under normal circumstances, all the data in the two application system servers in "Production Center A" are backed up in real time to the backup server storage in "Backup Center B" to ensure zero data loss, because this technology uses infinite incremental transmission, Therefore, even if it is transmitted remotely, it will not occupy too much bandwidth.
When the database data and file data of any application system server are wrong or lost due to logical errors (operating errors, mistaken deletion, etc.), the corresponding rollback data in "Backup Center B" can be restored at any time. The data at the rollback point is rolled back, and the data at the rollback point is guaranteed to be complete and available, and the data can be restored to the most recent complete state when the data is incomplete.
When any application system server suffers from hardware damage and data loss, after the server is repaired or replaced with a new server, it can be quickly restored to the previous complete state through the backup disaster recovery system, including applications, database data, raid, etc.

(image 3)
The proposal of this scheme fully considers the informatization characteristics of Sunrise Eastern Solar Co., Ltd. Based on the latest, most advanced and most stable technology, it adopts the most economical deployment mode and realizes a high disaster recovery backup Level of protection. It ensures zero data loss. When a logical error or hardware damage occurs, 100% data recovery can be achieved by rolling back at any point in time.
Real-time synchronization protection of important data on each server
Automatically monitor the database, continuously capture and backup data changes, as long as the data in the database changes, it will be backed up in real time and accurately. The security of data is ensured. Once data is lost or damaged, the data can be quickly restored from the backup machine.
The master database and the slave database can be synchronized in real time, eliminating the problem of interval backup loss in backup software. UPM also provides a complete no-data-loss mode and a business data correction method within seconds of loss.
Implementation of application switching within one minute when disaster occurs
When the main server goes down unexpectedly, the backup machine can take over the IP of the main server within one minute, provide all external services, ensure the continuity of the core business, and provide 365 days, 7*24 hours of uninterrupted business protection.
Implementation of original system recovery after disaster
After a disaster occurs, the original system must be restored as soon as possible. The reverse process of data disaster recovery and replication is performed during recovery, that is, reverse synchronization from the disaster recovery center to the primary data center. After the synchronization is completed, the application can be switched, and the entire system is restored to its original state.
Implementation of data recovery at any time for data logic errors
Data can be quickly restored according to any number of operation steps or time points, and return to any state of the database, so that data before accidental deletion or damage can be retrieved. During the recovery process, not only the integrity of the data is ensured, but the integrity of the event is also ensured. Solved the data logic error.